Case study: Avoiding submission to a hijacked journal

The ever-increasing number of journals in most disciplines can make it difficult to identify the right home for your research. What compounds this problem is the growing number of untrustworthy journals.
Let’s say you decide to stick to safe and reputable journals that you already know of and which your mentors or peers vouch for. Your submission/publication process can certainly be simpler then. But this still doesn’t mean you can let down your guard. That’s because, unfortunately, you can be tricked into submitting your manuscript to a fake, copycat journal that has stolen the identity of an authentic one.
Such a journal, called a hijacked journal, mimics an authentic journal’s website, luring unsuspecting authors into paying article-processing charges (APCs). The success of hijacked journals rides on authors’ trust in the journals they mimic, making this fraud tricky to recognize if you’re not careful.
Editage’s Publication Support team recently encountered a hijacked journal when helping a researcher get their manuscript published. Using this case study, I will try to show you what you can do to stay vigilant and avoid falling prey to such scams.
Sequence of events
Landing up on an incorrect website
The researcher in this case wanted to submit their manuscript to Central European Management Journal—which is published by Emerald Publishing and owned by Kozminski University, Poland. At the time, a Google search for this journal’s name brought up the following URL, which ranked high on the results page: http://journals.kozminski.cem-j.org/index.php/pl_cemj (now defunct).
Unfortunately, this was not the actual website of the journal—a fact that came to light later, as you will see.
Not hearing from the journal at all
The manuscript was submitted through the website mentioned above. But the author did not receive any acknowledgment. Over the next month and a half, the author contacted the journal to request an update but got no response.
Finally, an extensive online search helped identify the e-mail address of the editorial team at the authentic journal, and the author wrote to them. The journal informed the author that they had not received any submission from them.
Altering the course
The response from the authentic journal confirmed that the journal to which the author had submitted their manuscript was a fake one. The author wrote to the fake journal one last time, saying that if they received no response within three days, they would consider their submission withdrawn.
They still did not hear back and finally submitted their manuscript to the authentic journal. Their paper was eventually accepted and published there.
In this case, the author was fortunate that they did not pay any APCs to the hijacked journal and that the journal did not demand that they pay these charges up front or pay a withdrawal fee if they wanted to submit elsewhere. The lack of any communication from the journal, in fact, helped in eventually discovering that it was fake.
In other similar instances, authors have not been as fortunate.
What you can learn from this case
Don’t be misled by online search results
Hijacked journals often employ tactics that make their websites rank high in online searches for the journal titles they copy. In this case too, this tactic was what first misdirected the author to the wrong site.
Preferably, instead of looking for a journal’s homepage through a web search, use a reputable journal database or index—like Scopus, the Directory of Open Access Journals (DOAJ), or Web of Science. This reduces the chances of errors like this.
Bear in mind that some hijacked journals are known to have infiltrated these indexes as well, although the affected indexes do take corrective action and remove them.
Watch out for signs hinting at lack of trustworthiness
In whichever way you may have found a journal’s website, check it out carefully because even simple hints can help indicate that it may not be trustworthy.
For instance, in this case, the URL of the hijacked journal (http://journals.kozminski.cem-j.org/index.php/pl_cemj) appears genuine at a cursory glance, but you will still notice that it begins with http and not https.
That should be a red flag, because any site where you share/upload sensitive or confidential information (in this case, your research manuscript and personal/institutional details) needs to be secure and should begin with https. Reputable journals care about maintaining online security and the confidentiality of the submissions they receive.
Also, carefully check the information on the website for any other signs of fraud. Use the checklists and other resources provided by Think.Check.Submit. These can help you identify trustworthy publishers.
Examine other journal websites thrown up in online searches
Even if you do rely mainly on online searches of journal names, check out any other websites that come up, in case they lead you elsewhere. The URL of an authentic journal will very likely feature in the first page of the results.
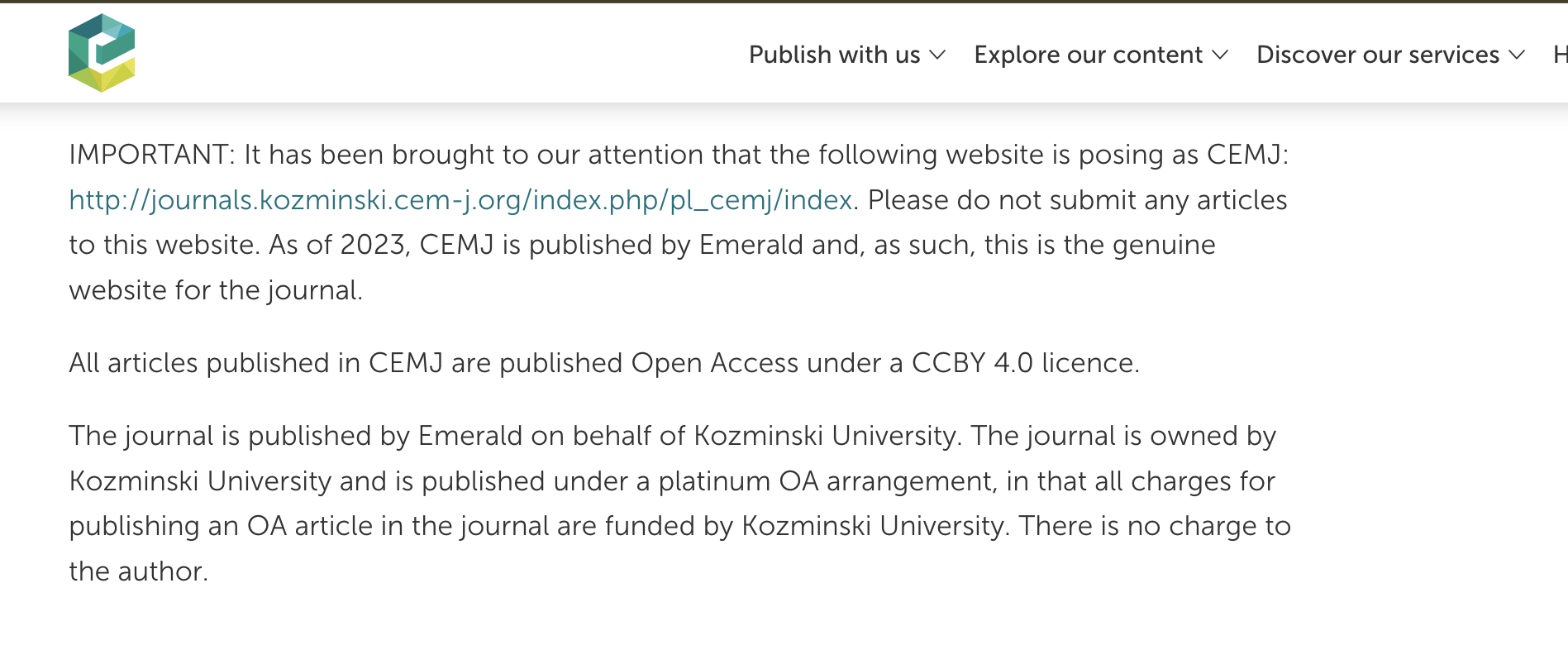
In the case of Central European Management Journal, the authentic URL does come up in the search results. And if you click on it, you’ll find that the home page explicitly warns authors about the hijacked journal (see screenshot below).
Refer to published lists of predatory and hijacked journals
The Retraction Watch Hijacked Journals Checker is an important resource that can help you avoid these journals. While it may not list every hijacked title, it is regularly updated. In fact, the fake journal mentioned in this case study features in this list (see screenshot below).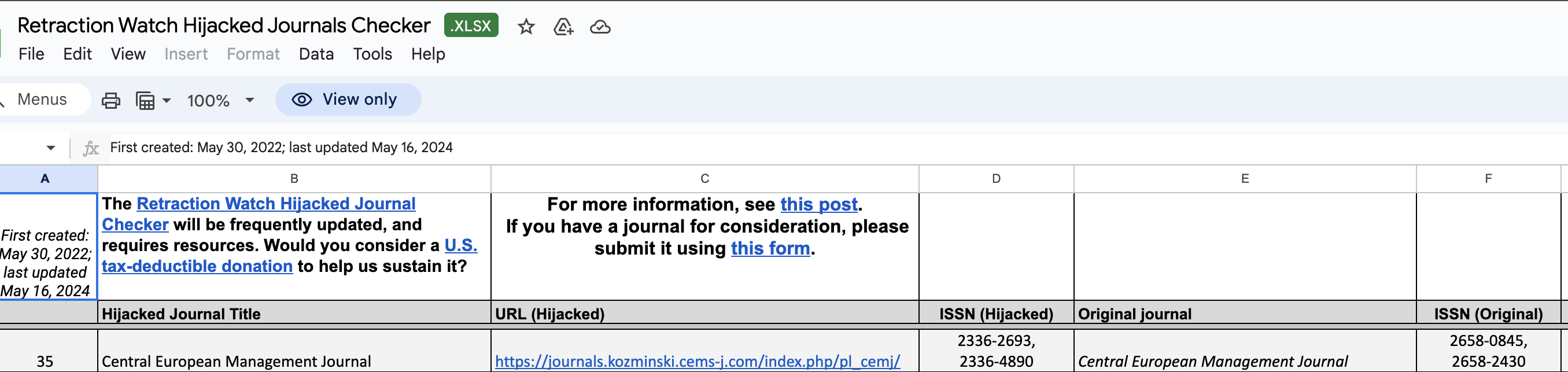
Note: The hijacked URL mentioned in this list begins with https, likely because the journal has updated it since.
Several authorities now provide regularly updated lists of predatory journals or other journals of questionable nature, including hijacked ones. Some might be paid, but others are available free of charge, especially any that may be maintained by your institute’s library or your funder. Find out if you can get access to these.
Cross-check the journal's open access model against multiple databases
If you read the full warning on the authentic journal’s website, you’ll see it clearly mentioning that the journal does not charge any fee to the author.
Predatory journals, including hijacked journals, exploit the gold open access model of publishing—that is, the model where authors pay APCs.
Gold open access journals charge APCs, whereas platinum/diamond open access journals don’t (read more about the different open access models here).
So, one level of check you should perform when you choose a journal is to find out which publishing model it uses. To do this, check out databases where the journal is indexed and read information about it.
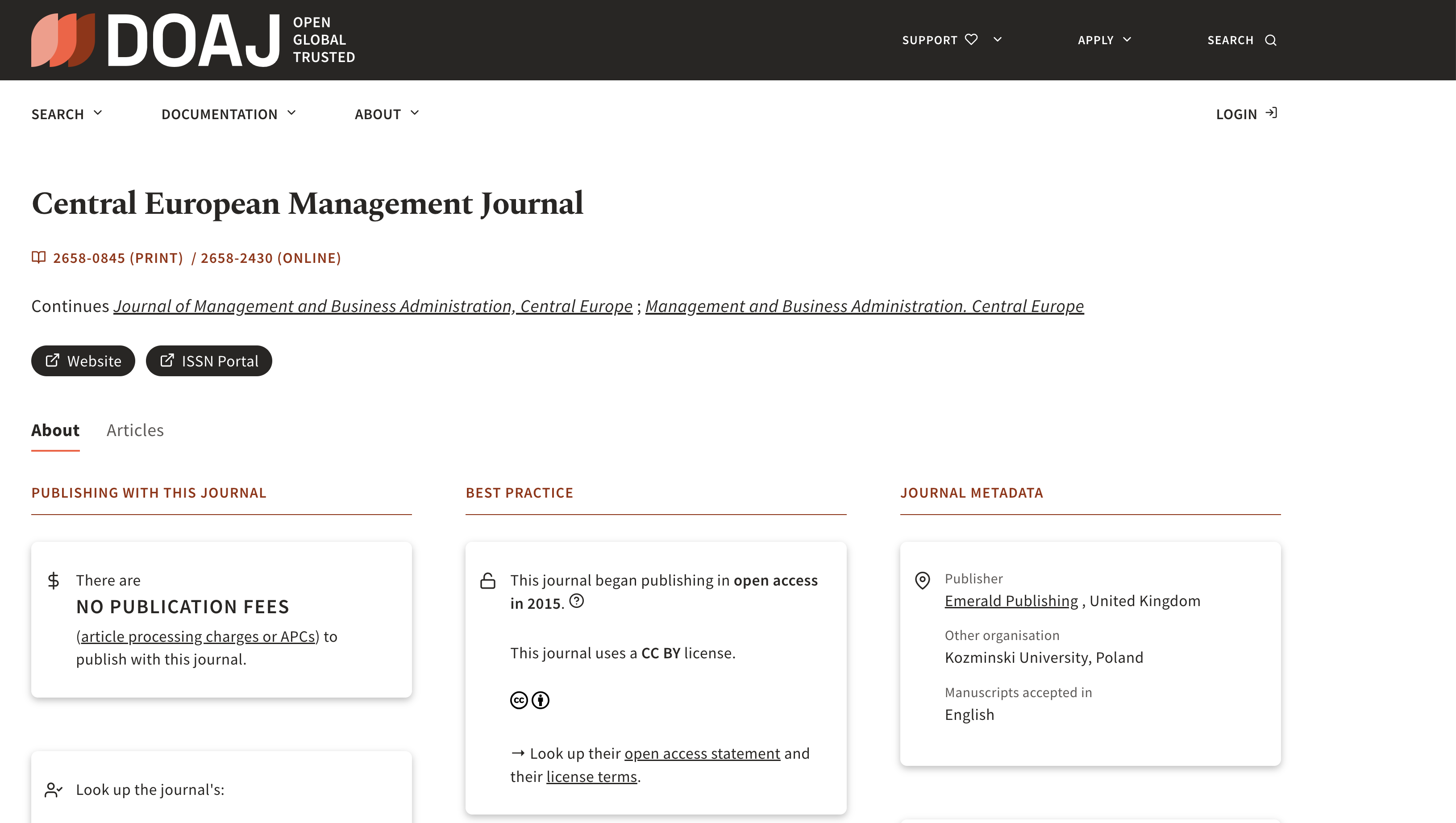
For example, if you looked up Central European Management Journal in DOAJ, you’ll find it clearly mentioned that it does not charge publication fees (see screenshot below).
Final thoughts
Like many other researchers, you may be under a lot of pressure to have a paper published in a certain category of journals by a specific time. But remember to not compromise on due caution. It pays to be extra careful at the time of selecting a journal and submitting your research to it. As this case shows, a few simple checks can save you time, money, stress, and potential damage to your reputation.
Comments
You're looking to give wings to your academic career and publication journey. We like that!
Why don't we give you complete access! Create a free account and get unlimited access to all resources & a vibrant researcher community.

Subscribe to Journal Submission & Peer Review










